Дополнительное описание
Main characteristics

 Appointment
Appointment
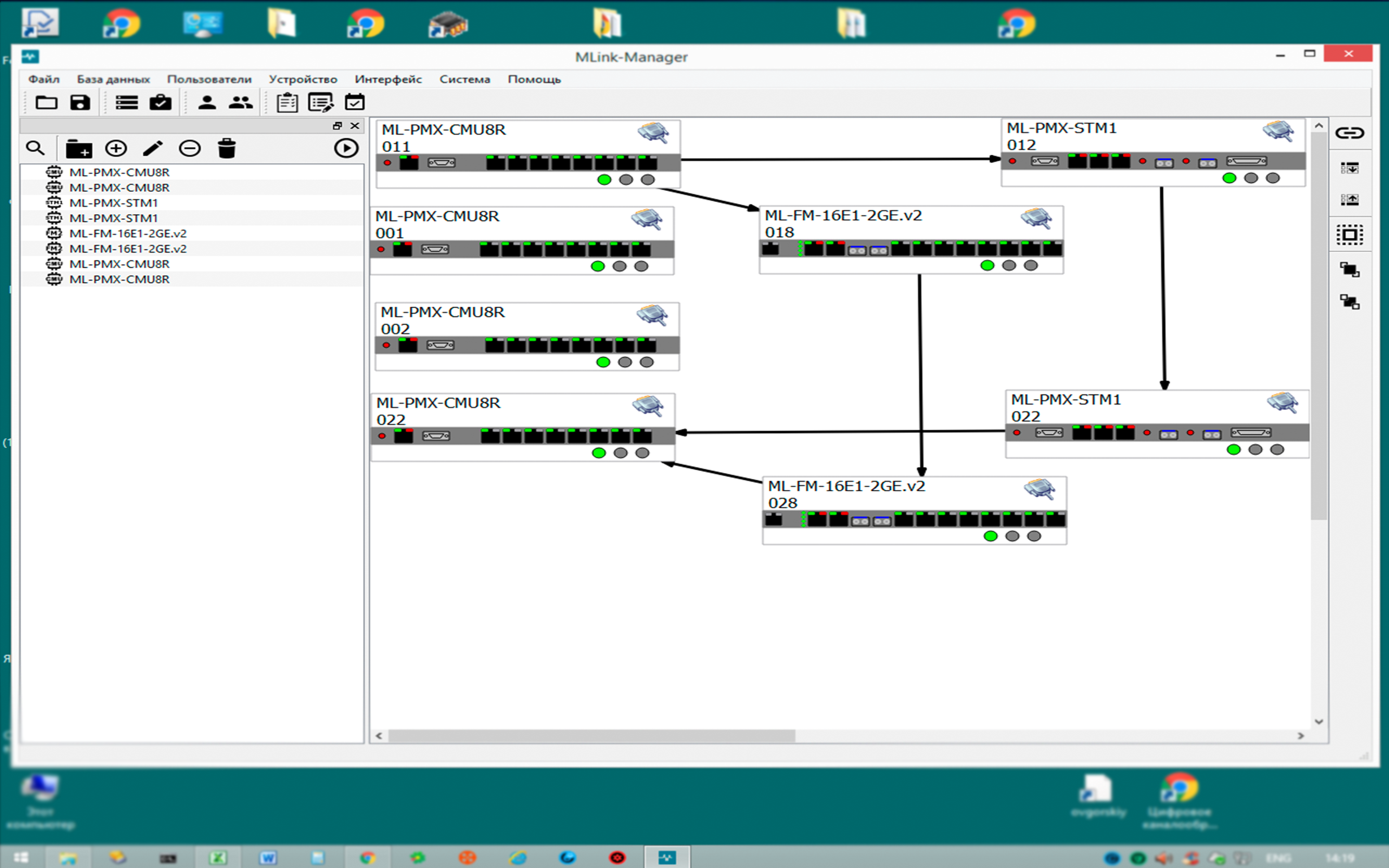
MLink-Manager allows you to monitor the status of devices and keep a history database. Poll devices is made through RS-232 and Ethernet. MLink-Manager supports data transfer protocols such as SNMP v1, v2, v3
 Functional safety capabilities
Functional safety capabilities
The main functionality MLink-Manager for Security include:
- identification and authentication of users to access;
- management of user access to objects;
- security audit.
 Data sources
Data sources
Data sources to gather information about the status of objects are:
- objects that are monitored by SNMP-request to the embedded agents;
- objects that send SNMP-traps;
- objects that are monitored via the ICMP-queries;
- objects that are monitored by different TCP-probe.
Control Objects
 MLink-PMX
MLink-PMX
Multifunction multiplexers. Support monitoring via SNMP protocol.
 MLink-FM / MLink-STM
MLink-FM / MLink-STM
Optical PDH / SDH-multiplexers. Provide building trunk optical communication lines PDH levels and from STM-1 to STM-64. Support monitoring via SNMP protocol.
 MLink-G
MLink-G
Radio-relay communication systems. Organization provide microwave communication links with a bandwidth of 2 Mbit / s to 2.5 Gb / s in a frequency range of 4 GHz to 86 GHz. Support monitoring via SNMP v2 / v3 protocol.
 ML/SL-IPSW
ML/SL-IPSW
Multifunction switches / routers support monitoring via SNMPv2 / v3 protocols, Telnet, SSH.
 MLink-UPS
MLink-UPS
Uninterruptible power supplies ML-UPS. Support monitoring via SNMP protocol.
 Equipment party
Equipment party
Support monitoring via SNMP protocol.

Application
 The operational monitoring and control
The operational monitoring and control
 User identification and authentication
User identification and authentication
 Increase operational efficiency
Increase operational efficiency
software and hardware systems by automating the processes controlling their generalized state, reducing the time unavailability of equipment and communication channels between them, reducing the time localization of the causes of malfunction of the equipment
 Fast access
Fast access
to programs network monitoring and management, specific to each type of equipment. Security Compliance
 Detection and minimization
Detection and minimization
negative impacts of emergency situations arising in the information and telecommunications infrastructure. Presentation of exploiting personnel complete information about the condition and performance of the equipment

 Certificate
Certificate
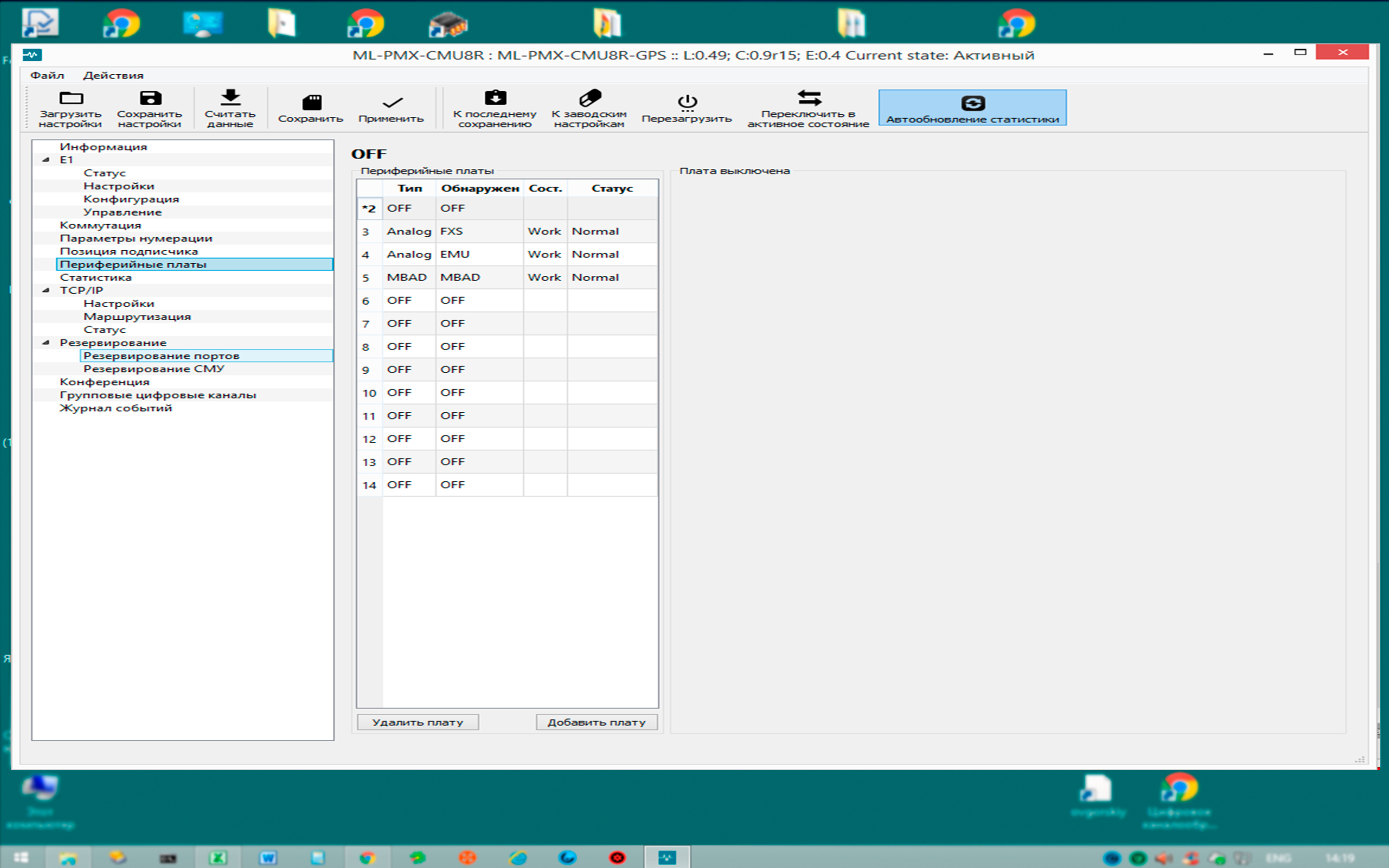
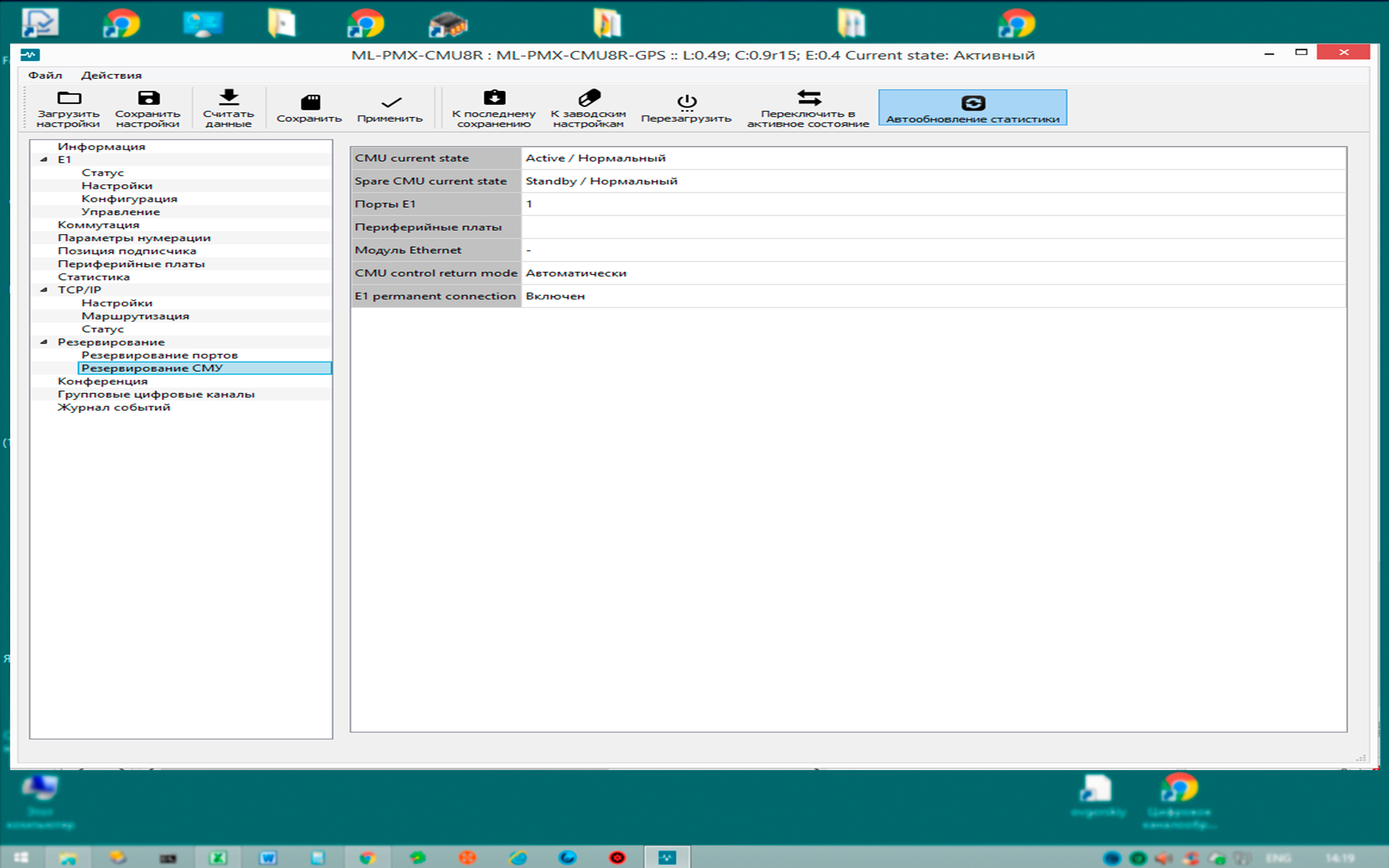

 Appointment
Appointment